JCA - Java Cryptography Architecture
JCA framework is used when you need to work with security using cryptography. A little obvious 🤔. But when is necessary to use cryptography? It is a really important question. 😎
Scenario
A very known scenario is the one where you will have Bob and Lisa trying to communicate with each other in a safe mode. In the same way, a usual case is related to the transaction of money. For sure, when involved our wallet we really are worried. 👩🏽✈️
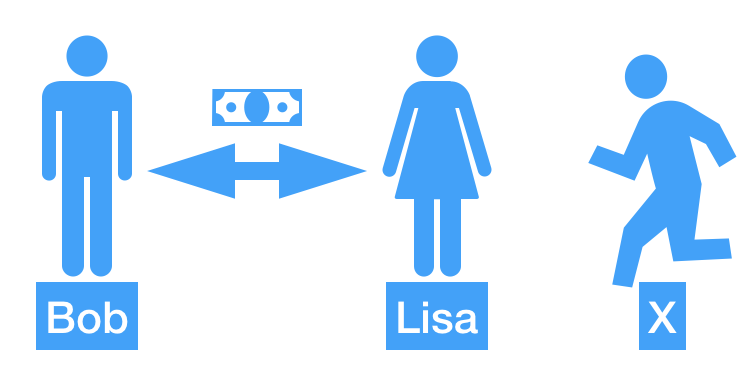
What is the guarantee to Lisa that Bob is really Bob? How Bob can be sure that Lisa is who she says to be? How they can do the exchange protected of the other person X?
Yes. You know the answer and thas why you are reading this post. 🤓 . JCA is the option of this post.
The message transferred between them should be private to X doesn't know what they are exchanging, such as credit card. If X doesn't know the password he cannot get the money.
Then, Bob and Lisa need to know the password. How to transfer the password safe of the X?
Keys
From these scenarios, you have the concepts of the public key and private key. The public key is what you will share with everyone, even X. And the private key is what will be safe with you.
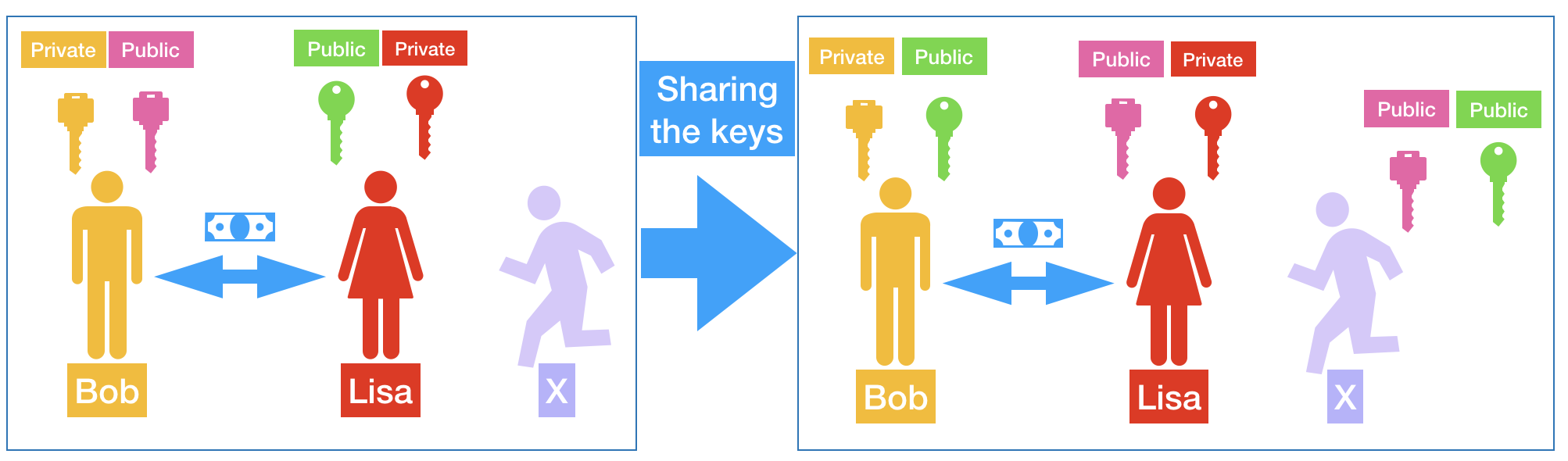
So, Bob has a public and private key, such as Lisa. They sharing them public keys with everyone, including the X. With Lisa's public key shared with Bob, he can send a message to Lisa where only she can read. It happens because Bob uses Lisa's public key to package a message and Lisa Will use her private key to unpackage that. Only Lisa's private key can unpackage a message packaged with her public key. So, even if X catch the message he could not unpackage that because he has only Lisa's public key.
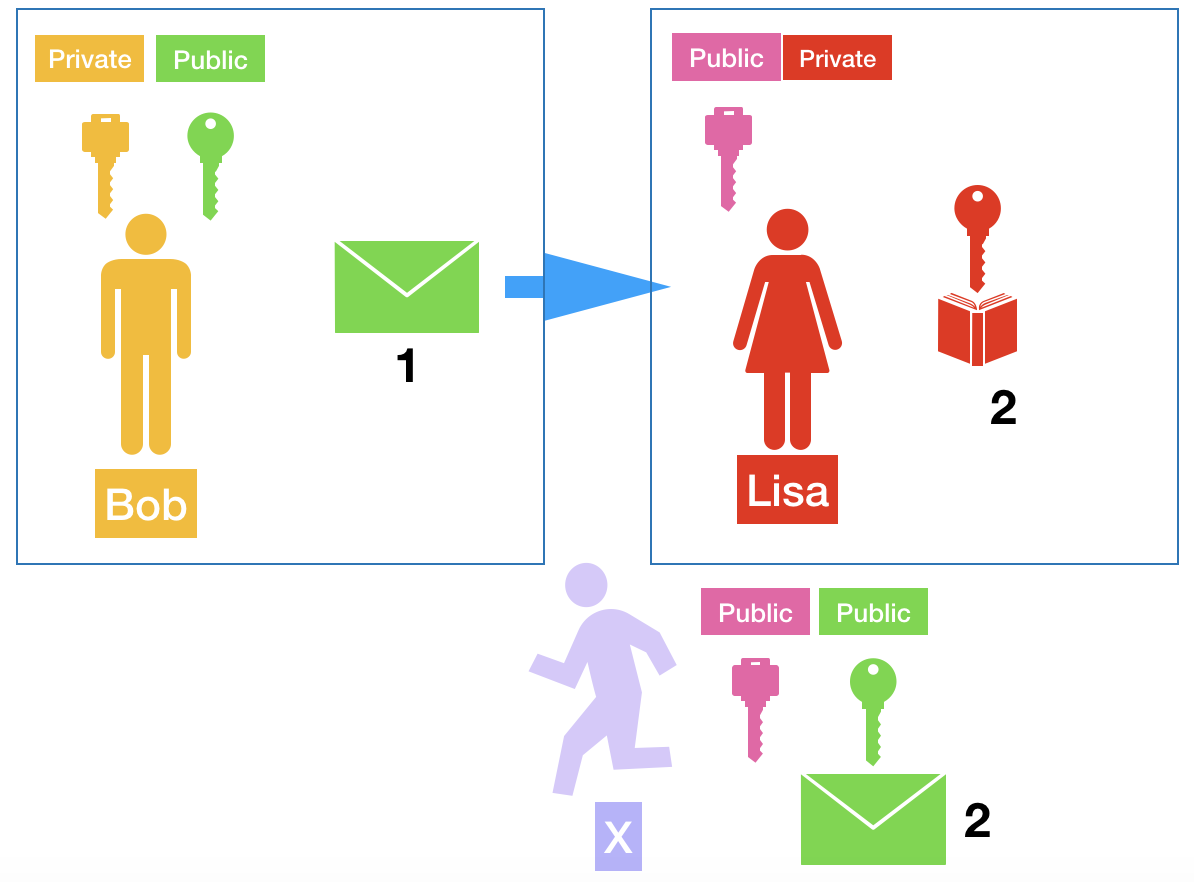
Conceptually, if you are using the public and private key, the algorithm is asymmetric. If you use only one key (no private key) you are using the symmetric algorithm.
Now you have the main idea and we can use the JCA.
Hands-on
The JCA can support you to work, for example, with message digests, digital signatures, encryption and key generation.
Message Digest
It can be used to guarantee that the message is not modified. The message digest is a hash value calculated from the original message and encrypted together with the message. When this data is decrypted the message has to calculate the same hash value.
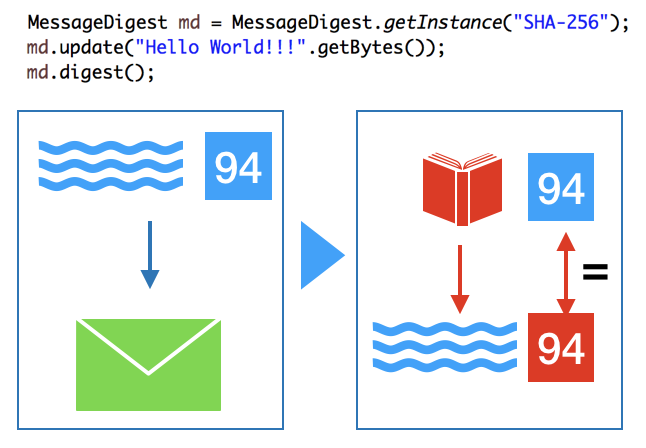
The algorithms supported to convert the message to a message digest are such as SHA-1, SHA-256, MD5.
Keys
The keys are values used to encrypt and decrypt the message. In other words, make the message not easily read. If the process uses the same key to both operation so it is using a symmetric algorithm. However, if it uses different keys (public and private) is using an asymmetric algorithm. The class used to generate the keys is KeyGenerator and KeyPairGenerator.
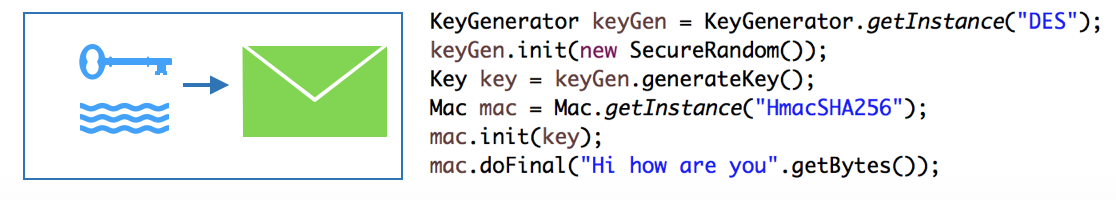
MAC (Message Authentication Code)
The MAC is used to provide message authentication with a symmetric algorithm, which uses only one key shared with everyone. It is similar to digest but adding a key to encrypt.
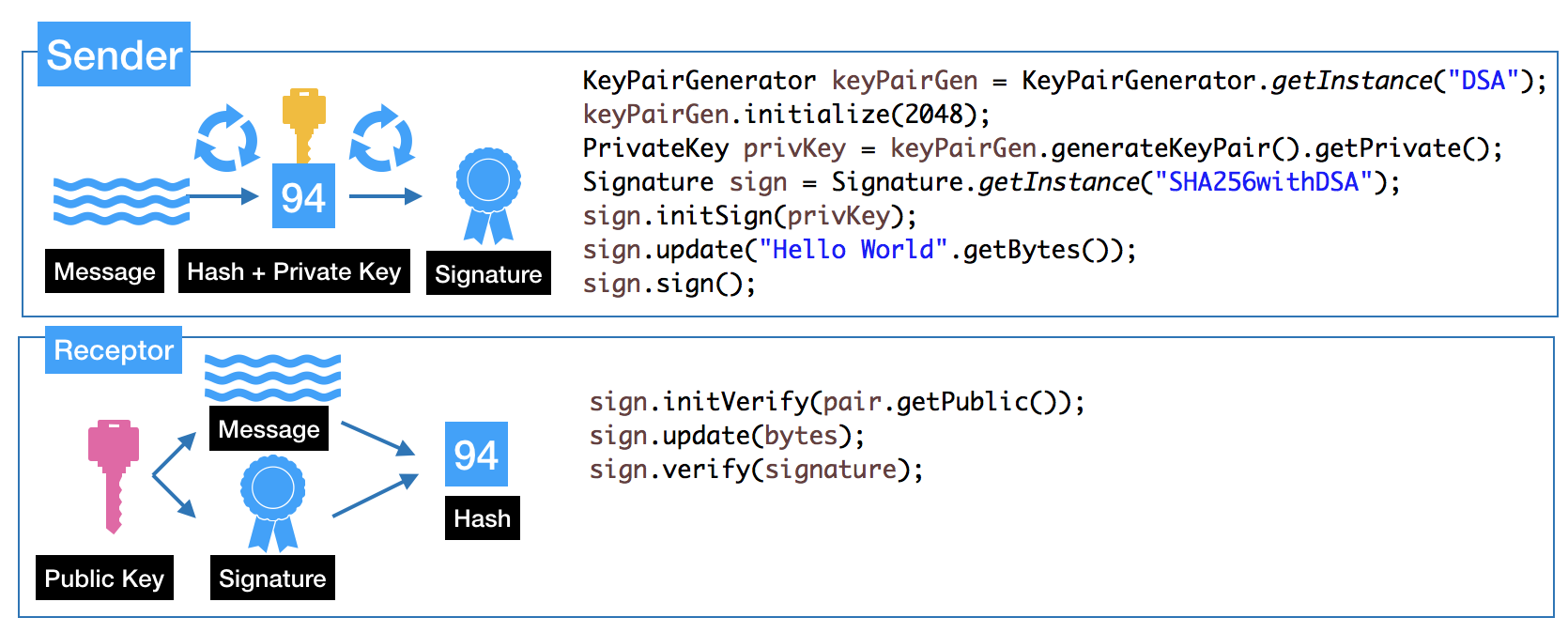
Digital Signature
It will give guarantees about the sender because this process envolve the private key. First is created the hash, after that the value is encrypted with the private key.
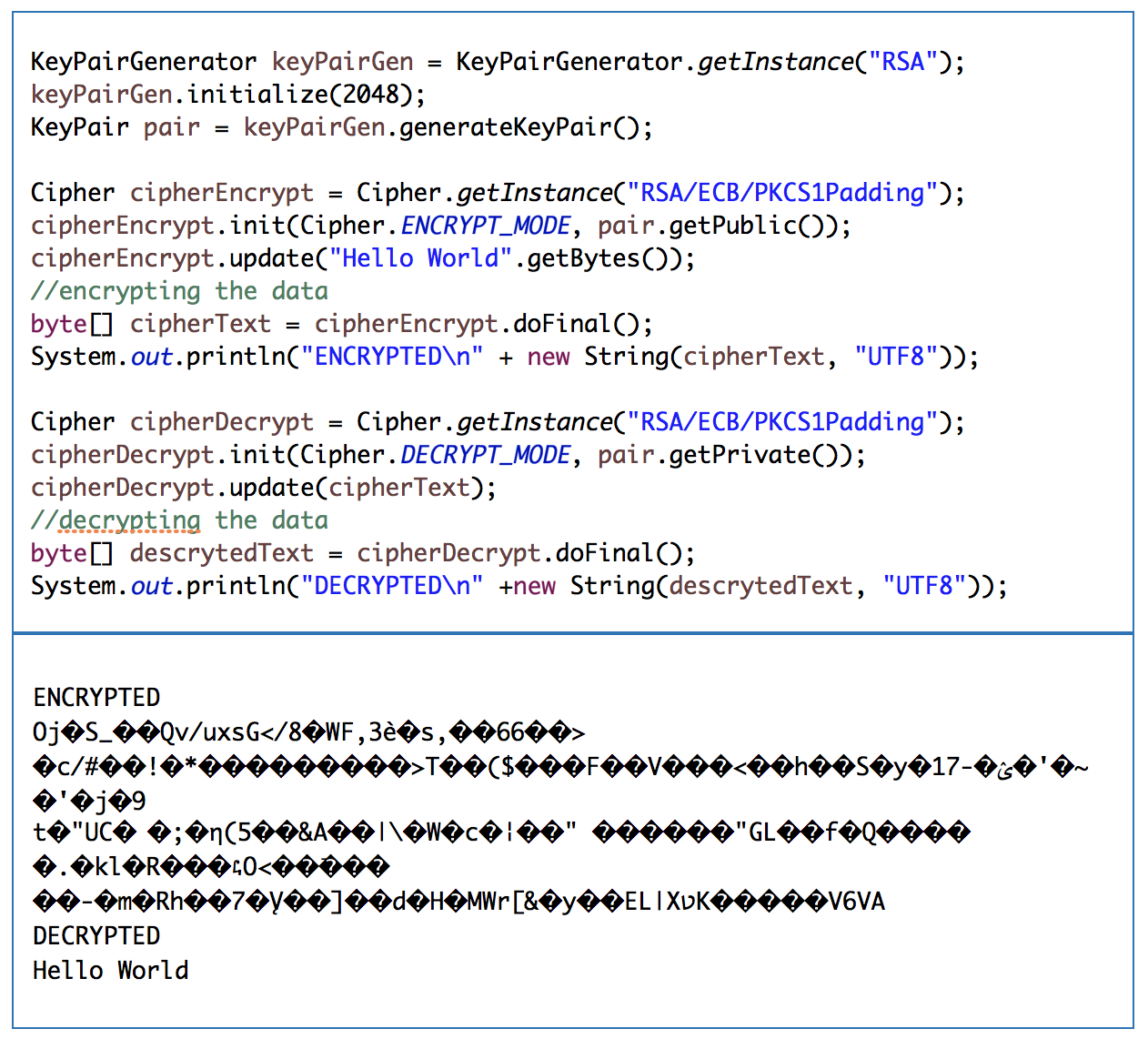
Encrypt/Decrypt
The Cipher class will give support to this process. It represents a cryptographic algorithm. So, you will need of the public key to encrypt and private key to decrypt the message.
References
- http://tutorials.jenkov.com/java-cryptography/index.html
- https://www.tutorialspoint.com/java_cryptography/java_cryptography_introduction.htm
- https://dzone.com/articles/java-cryptography-simplified-part-1